In a recent social-engineering attack targeting the hospitality sector observed by the ThreatSpike team, there appears to be a change in the tactics employed by the threat actor. The hospitality sector, where top-notch customer-service is expected, customer-facing employees are often lucrative targets for phishing, as detailed in our previous blog post. While phishing email is still a common social engineering vector, we have observed the threat actors are now also using other methods, such as vishing or even the use of chatbot functionality, to engage with the target employees. More interestingly, we have also observed an unconventional payload delivery chain where the malicious executable, an infostealer, is fetched via SMB File Share and executed in memory.
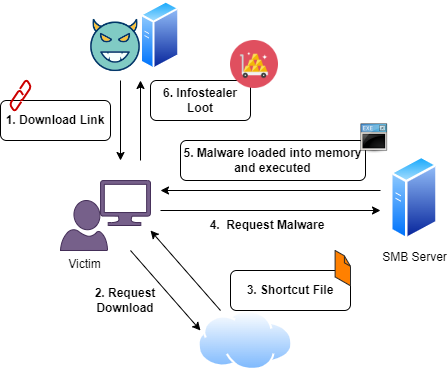
Delivery
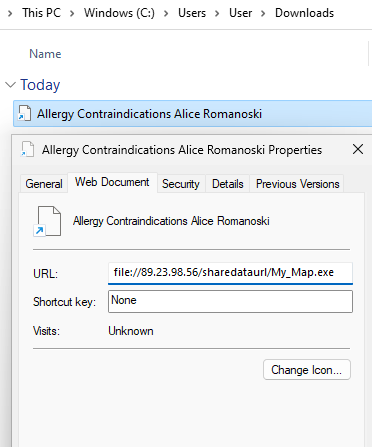
The threat actor first engages the customer-service employee via the chatbot functionality, A download link was provided to the employee which downloads a shortcut file (.url). From Figure 2, we can see that the target URL is set to a UNC file path of an executable “My_Map.exe” in an external file share 89.23.98.56/sharedataurl. Another executable found on the shared drive is url-map lidia.exe
When the user clicks on the shortcut file, a prompt is shown to ask if the user wants to open the shortcut file and to run the executable. This is due to the Mark-of-The-Web (MOTW), informing the user that the file originates from the internet or outside the local network.
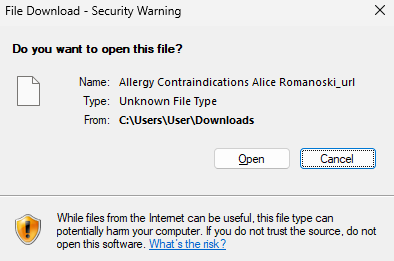
Figure 3. Mark-of-The-Web (MOTW) warnings
Besides the MOTW protection warnings shown to the victim, the subsequent payload delivery mechanism has evasive capabilities as the executable is fetched via SMB and loaded into memory without touching the disk. By loading the file via SMB, it does not use the usual channel of HTTP(s) download, which would likely be heavily monitored. Secondly, the executable is loaded directly into memory without existing on the disk, this prevents Anti-Virus solutions from scanning the file on disk.
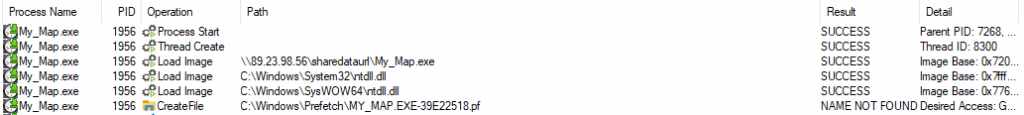
Figure 4. Executable image loaded from SMB Share without being downloaded to local disk
Payload Execution
Similar to previous phishing attempts observed, the payload is an infostealer which targets credentials stored on the host device. The infostealer first enumerates system information before searching the host device for browser stored credentials and cookies. Several browsers such as Edge, Google Chrome, Brave and QQBrowser. The infostealer also enumerates the device for crypto wallets and chat apps such as Discord, Telegram and Tox. The harvested data is exfiltrated via HTTP to slot0.openbeecluod.com.
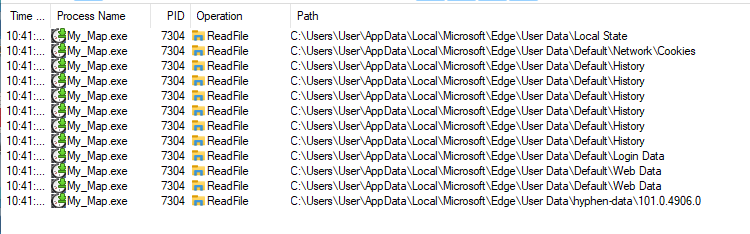
Figure 5. Edge browser data file reads
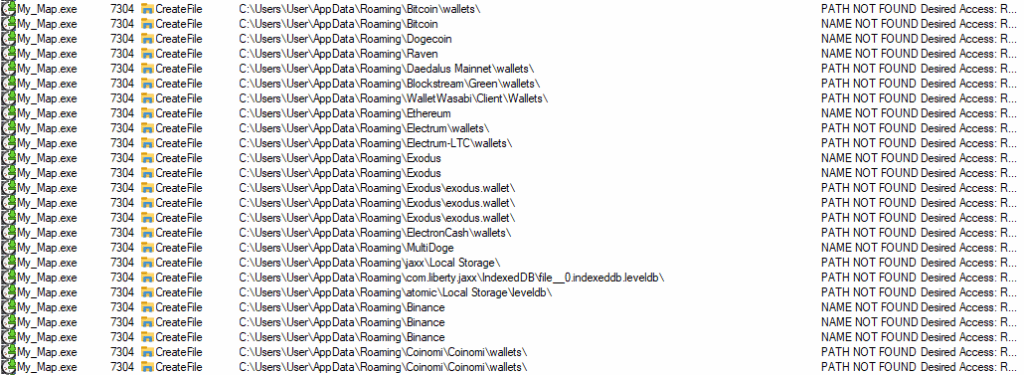
Figure 6. Crypto wallet enumeration
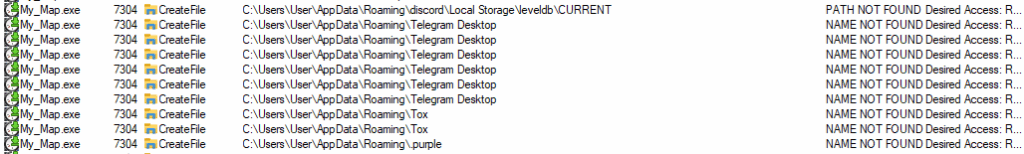
Figure 7. Chat App enumeration
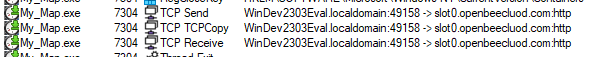
Figure 8. Exfiltration via HTTP
At the time of the incident, the malware sample had not been uploaded to VirusTotal. However, from analysis, the sample is exfiltrating the data to slot0.openbeecluod.com (109.206.243.134) and is likely to be a Stealc infostealer based on the C2 IP.
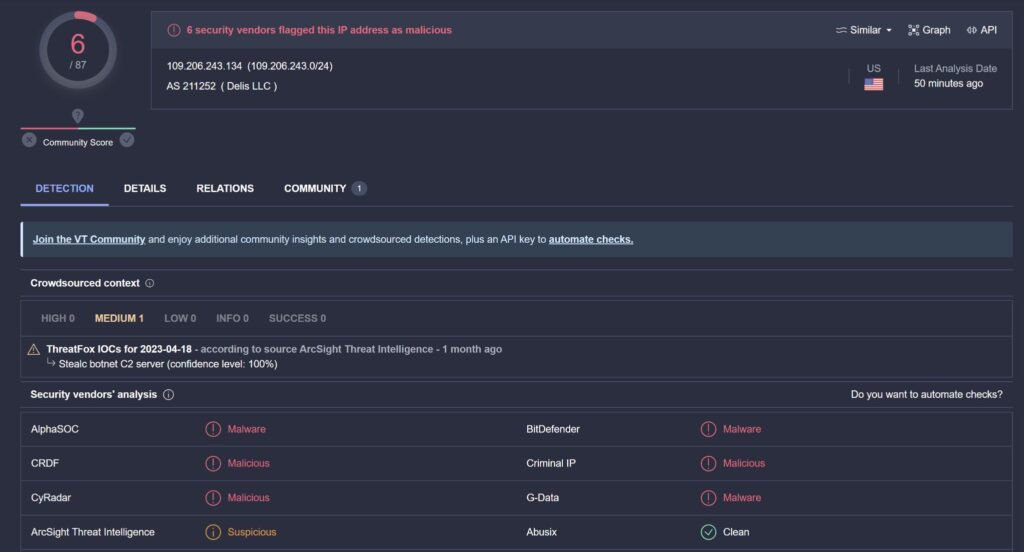
Figure 9. Stealc C2 IP on VirusTotal
Interestingly, from analysis of related files to the SMB Share IP address, the majority of the samples were related to the RedLine stealer.
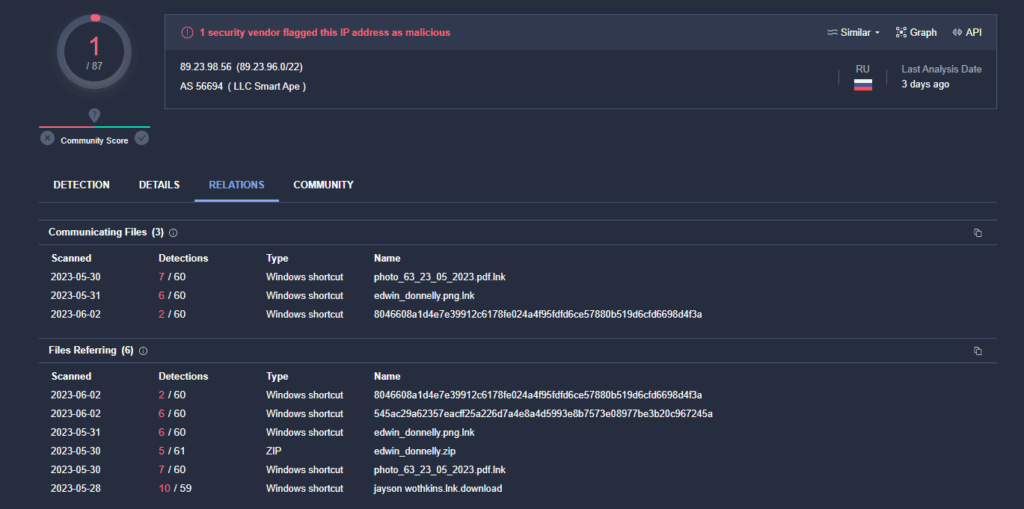
Figure 10. SMB file share IP on VirusTotal showing the related files which are RedLine Samples
Mitigation
In order to mitigate against this attack vector of execution of payload via SMB share, it is recommended to block any connections to external SMB shares if there is no business need. Otherwise, external SMB connections should be allowed on a allow-list basis. Training employees to identify MOTW warnings and reporting phishing incidents can also help deter similar attacks.
ATT&CK Techniques
- T1566.002 Spear-phishing Link
- T1566.003 Spear-phishing via Service
- T1082 System Information Discovery
- T1083 File and Directory Discovery
- T1555 Credentials from Web Browsers
- T1539 Steal Web Session Cookie
- T1020.001 Automated Exfiltration
IOCs
Files
| FILE NAME | SHA256 HASH |
|---|---|
| Allergy Contraindications Alice Romanoski.url | A260523CDA19B3B219E5DE2BCBB33D0375BA194BC98A7EE1EEBF3EA1B94B367A |
| My_Map.exe | 49499904D723904172E88C58036CB4058A6FCF0876197646C9262CB32C1ABC86 |
| url-map lidia.exe | 13d1bc55374e37c5abd314efc92b3890dccca2a1d9ed5bfb1bde0f825e9f87e5 |
Network
- 89.23.98.56
- 109.206.243.134 (slot0.openbeecluod.com)