Protection everywhere
Devices are continuously monitored by our cloud service and protective controls are applied wherever your devices are located, whether that be in the office or on public Wifi.
We monitor networks for a broad range of security issues, tailoring our monitoring for the specific industry and requirements of each customer.
We monitor for hacking including reconnaissance, network and application exploits as well as lateral movement.
We use methods including machine learning to detect malicious executables, command and control activity as well as network propagation.
We monitor for weaknesses in technology systems and business processes that may be used to steal data and commit fraud.
We monitor logins, authorisation changes, access reach, electronic communications and data transfers to detect insider threats.

Devices are continuously monitored by our cloud service and protective controls are applied wherever your devices are located, whether that be in the office or on public Wifi.
We provide extensive functionality that our customers can use to secure their environments and all functionality is provided as part of a single license.
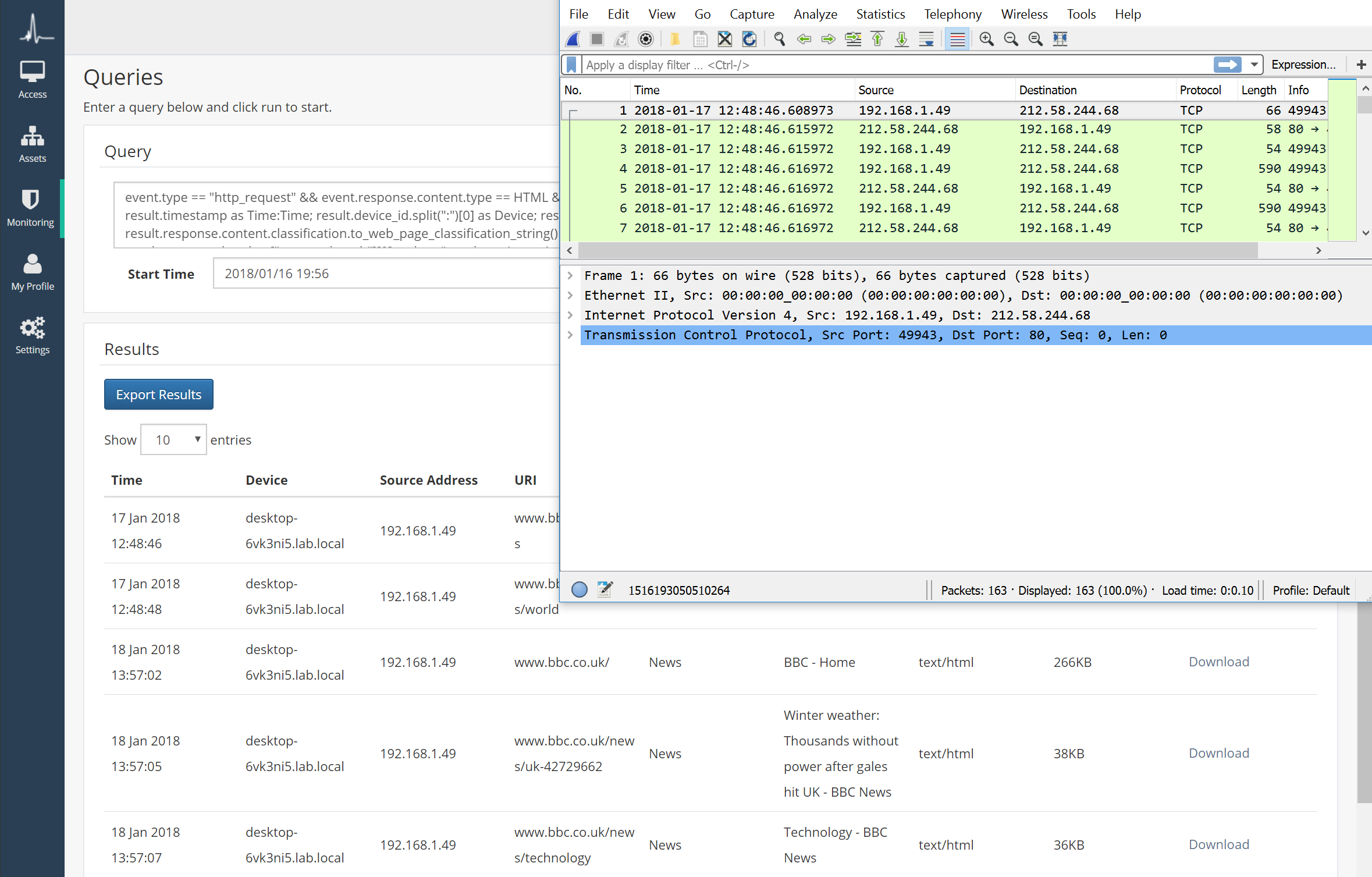
ThreatSpike delivers deep insight into activity on the network:
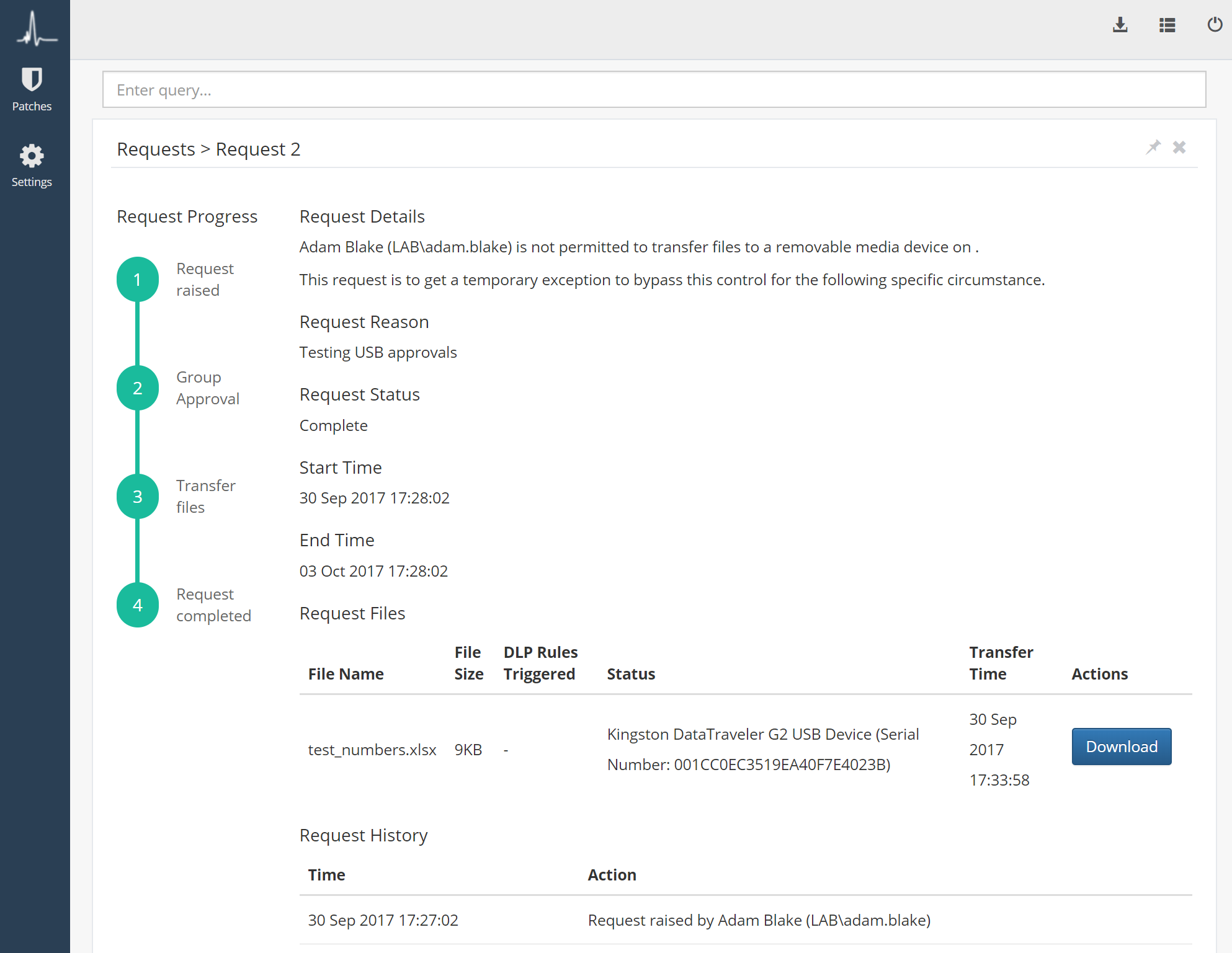
ThreatSpike can be used to protect against data leakage:
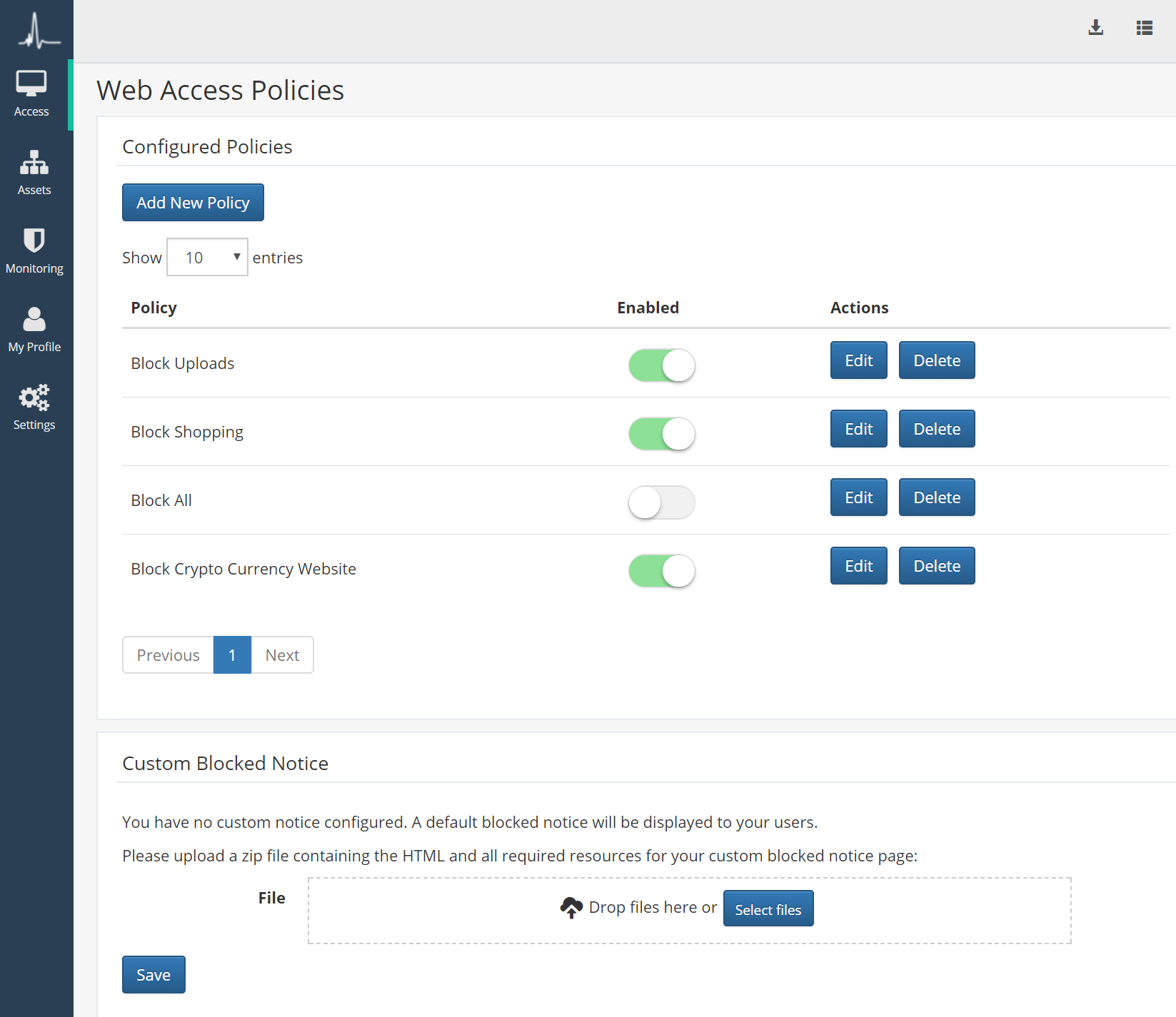
Web browsing can be restricted to ensure compliance with corporate policies.
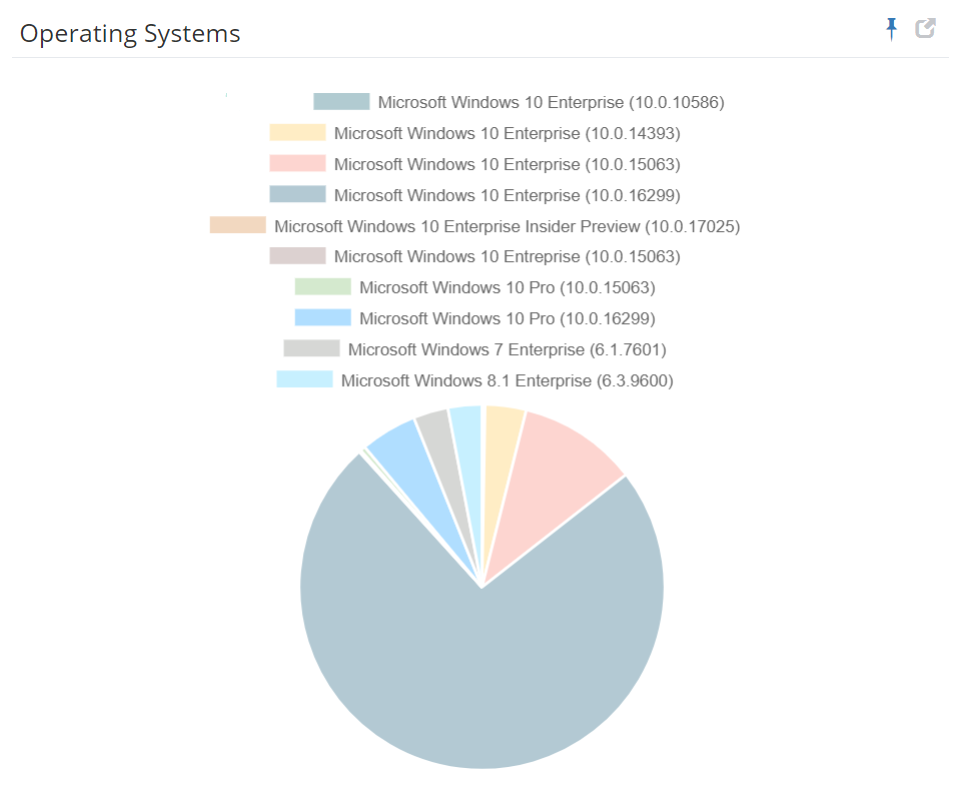
Information about devices is collected and presented through dashboards and reports, including:
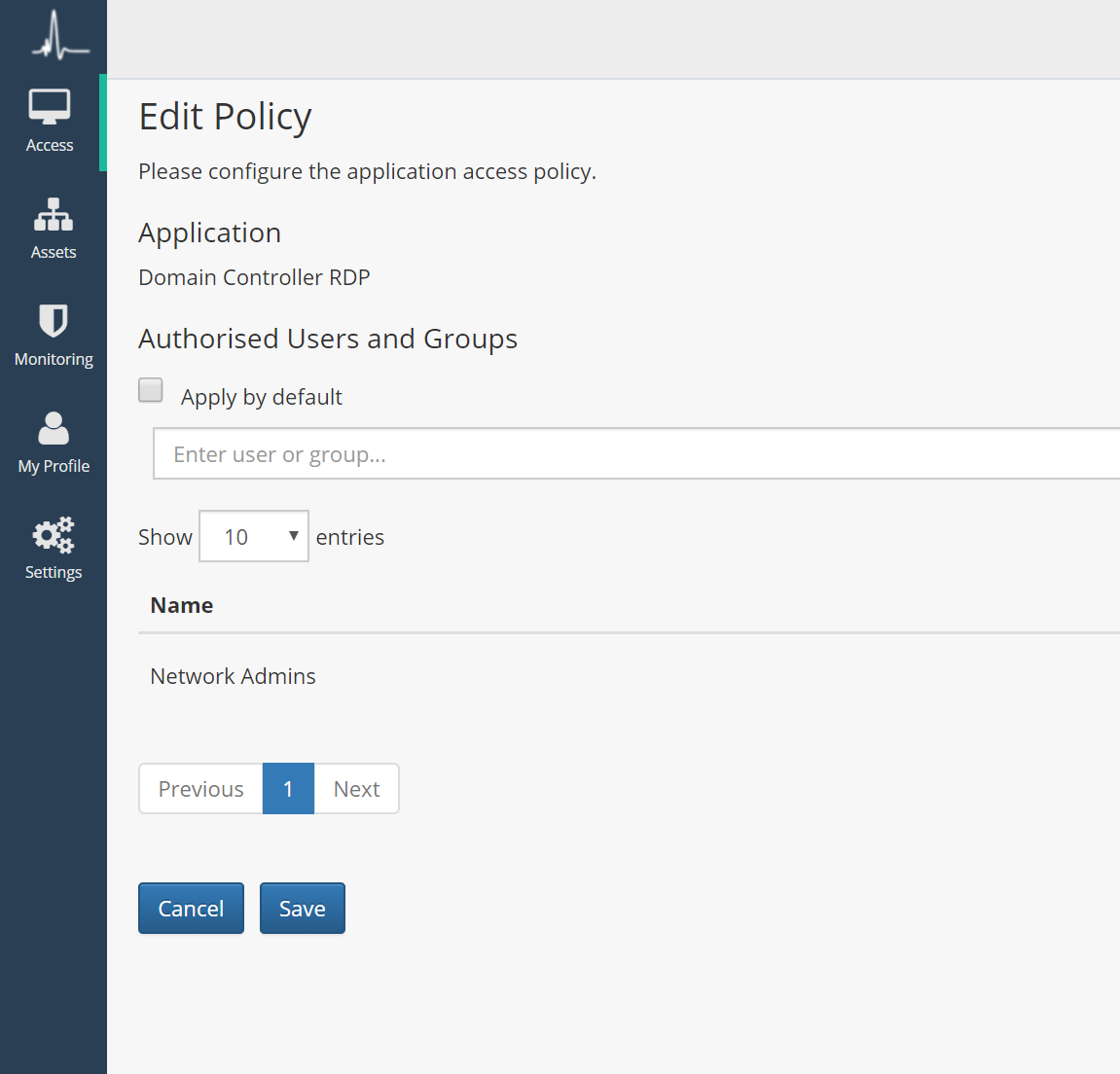
Access to internal systems on the network can be restricted to increase security and mitigate worm propagation.
We offer the first ever fully transparent, predictable pricing model for a managed security service. We do not rely on 3rd parties and our technology is developed entirely in-house, allowing us to stay agile and avoid passing on unnecessary costs to our customers.
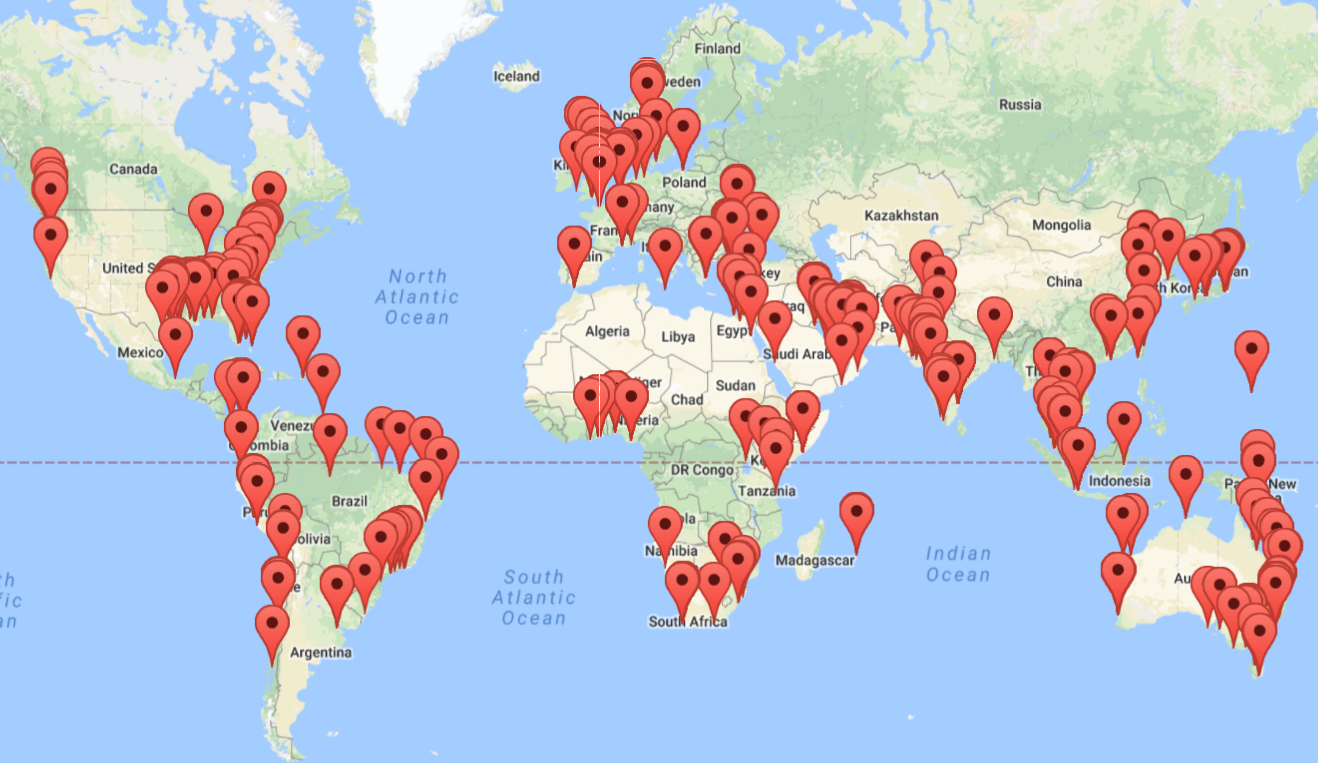
We provide monitoring services to companies ranging from 10 to 100,000 users spanning 15 industries and 50 countries.

"ThreatSpike offers a strong value proposition that ties in to our business needs. Our experience with ThreatSpike is extremely positive. Like us, it is a dynamic, entrepreneurial organisation and quick to respond to our changing requirements."

"ThreatSpike analysts provide us with assurance that our network and customer data is constantly protected and that when a threat is detected, that it is dealt with quickly."










ThreatSpike protects customers and devices all across the world each day. With such breadth comes the ability to identify threats as they are arising and develop more capable and accurate algorithms.
Average number of issues discovered during trials
Million events analysed per day
GB of network traffic analysed per day
If you have questions which are not featured here then please drop us an email.
Installation is very quick - all that is required is to deploy an installer to the machines in the network. If a software distribution tool isn't available then we can provide a script to do this. Once deployed, we begin monitoring without any assistance from your team and if we see an issue we raise this with you via email. It is then up to you whether the issue warrants remediation.
Our software can run in two modes - mirror mode and inline. In mirror mode a copy of the traffic is taken and analysed and there is no impact to the network. In inline mode, which is required for functionality which changes the network traffic (e.g. web filtering, SSL/TLS inspection), there is a reduction in the network bandwidth proportional to the CPU performance, however this is very rarely perceivable by the user.
The security of your data is our main concern and we follow industry best practices at all times. Notably we own and manage our own server infrastructure which is hosted in a tier III data center in London and access is highly restricted. We use firewalls to restrict network access, all access to servers is logged, we do not share your data or access to any of our systems with anybody including 3rd parties. We encrypt all data at rest and in transit.
Log management is complex and also expensive to deploy and manage. Compared to log management which requires taking in feeds from existing products on the network, our technology monitors network traffic directly to build event data which is then correlated within our cloud. It can be deployed very quickly, entirely standalone.
Yes, we provide both the technology to collect and generate logs, as well as the day-to-day analysis of those logs by trained security professionals. Usually our customers find that we are able to provide both at a lower cost than our competitors who are offering just a log management product.
We support Windows, macOS and Linux. We can also provide hardware sensors capable of monitoring all endpoints on the network.